
Vulnerability Scanning: Ensuring Cybersecurity in the Digital Age
An in-depth exploration of vulnerability scanning, its importance, methodologies, and best practices to safeguard against cyber threats.

An in-depth exploration of vulnerability scanning, its importance, methodologies, and best practices to safeguard against cyber threats.
An in-depth exploration of software architecture, its importance, various styles, and best practices to ensure robust and scalable software systems.
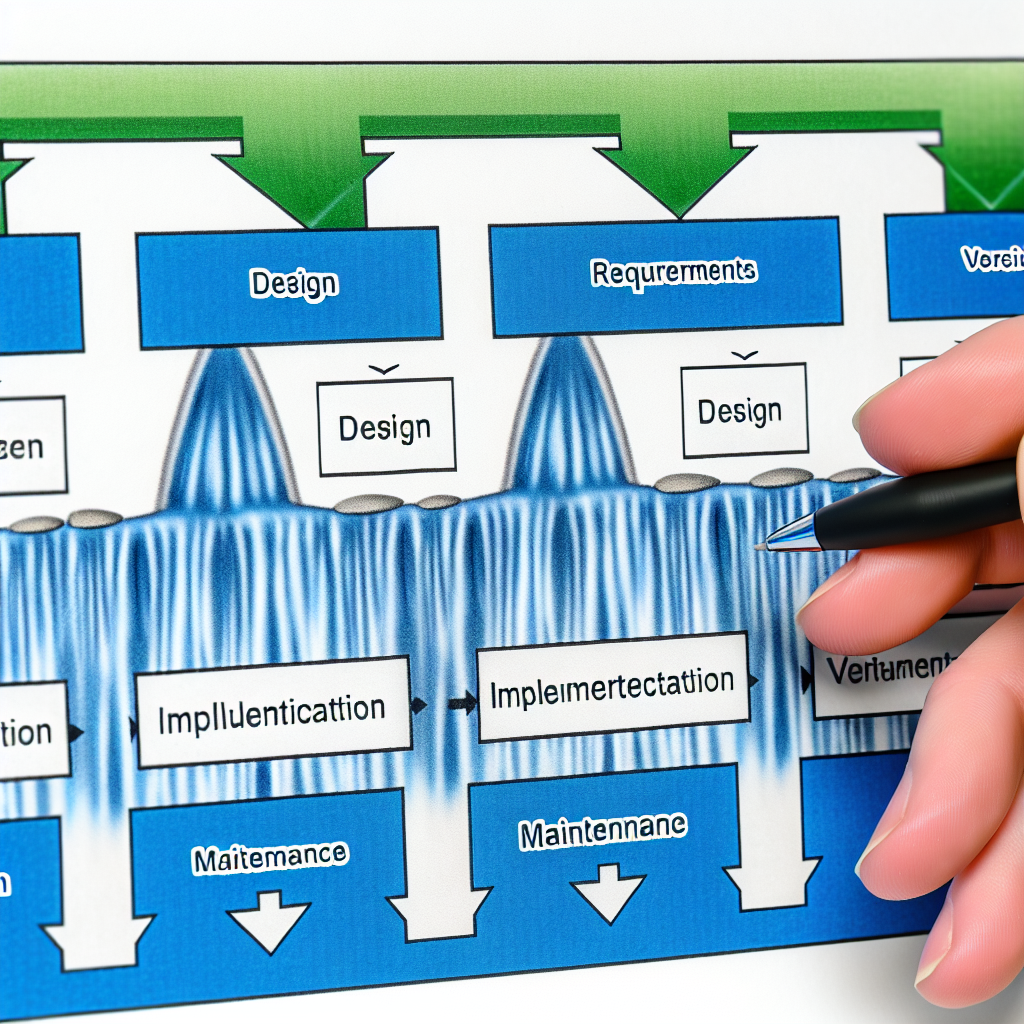
Discover the Waterfall Model, a traditional project management approach emphasizing sequential phases, from requirements to maintenance.

Explore how socket programming can be adapted for rodents, covering foundational concepts, practical applications, and the potential benefits for research.

A detailed exploration into backend development, covering its definition, importance, technologies, and best practices.