
Network Security Incident Investigation
A comprehensive guide on investigating network security incidents, covering methodologies, tools, and best practices.

A comprehensive guide on investigating network security incidents, covering methodologies, tools, and best practices.

Database masking is a crucial technique for protecting sensitive data by concealing it from unauthorized access, ensuring privacy and security.

A comprehensive guide to understanding the requirements and processes of security incident regulatory reporting for organizations.

A comprehensive guide to understanding the intricacies of software project management, its methodologies, essential skills, and common challenges.
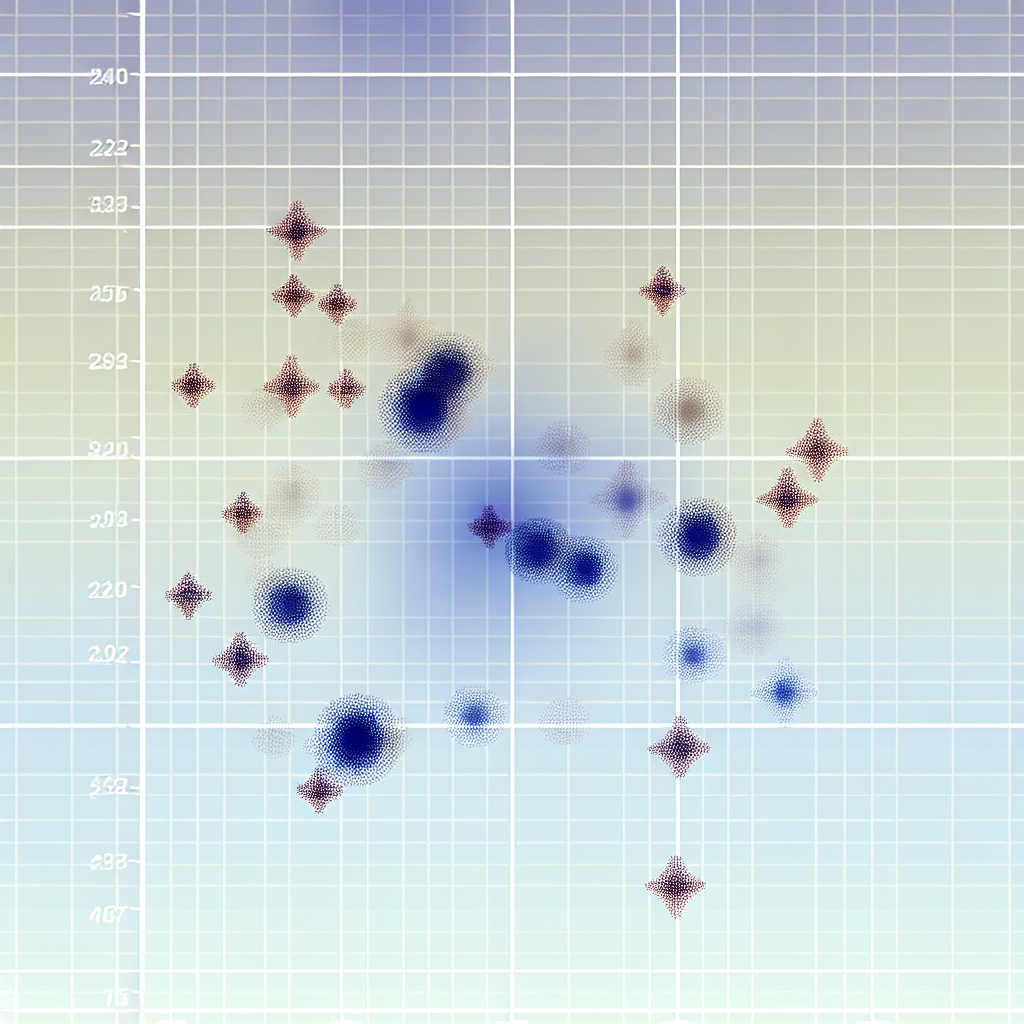
An in-depth exploration of K-means clustering, its methodology, applications, advantages, and limitations in data analysis and machine learning.